HTB uni CTF 2023 - WindowOfOpportunity [Easy]
A simple revers flag cracker challange with only a binary file.
Let’s get started by executing the binary.
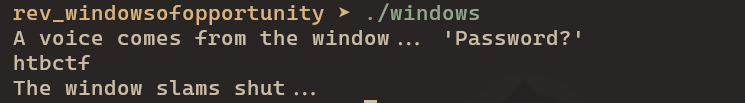
Hmmm. It is asking for some sort of ‘Password’, looks like the flag might be the password.
Analysis
Open the binary in Ghidra and see what’s inside.
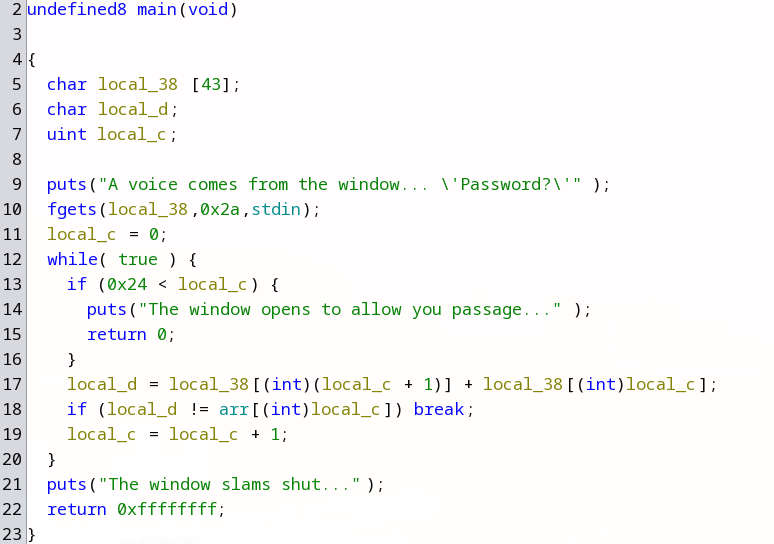
The program is quite simple, it takes the input from the user, iterates through each character while doing some operations and then compares the result with ‘arr’ array. If the current result does not match, the program exit with a message “The window slams shut” . If all results match, the program exit with “The window opens to allow you passage…”
Change the name of each variable to make it more readable.
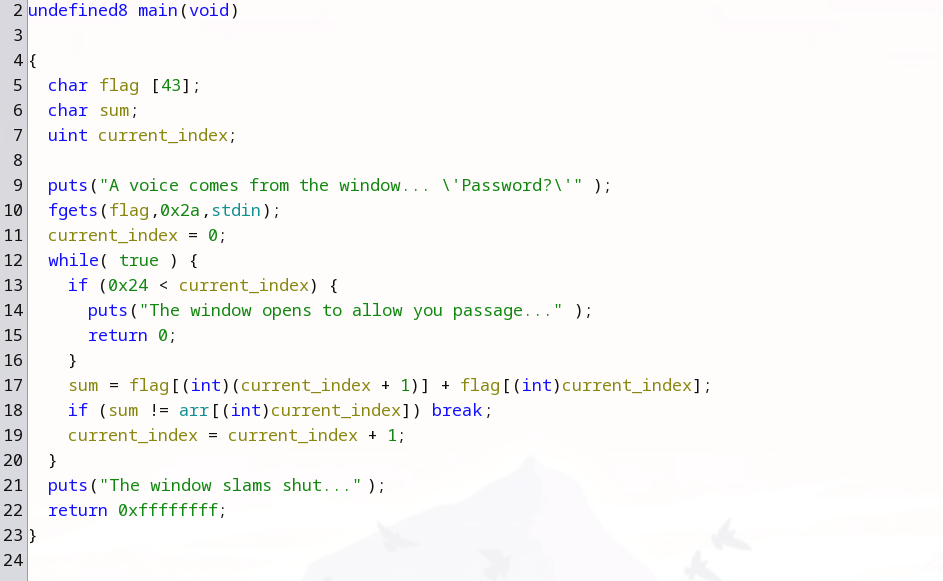
Now, it is easier to see how the program checks the user input. It takes two characters (the current_index and current_index + 1), then sum them up and compare with the value (with the same index) in the ‘arr’ array. Therefore, we just need to find values stored in the ‘arr’ array.
I found the values by running the program with gdb, disassemble the main function we can see :
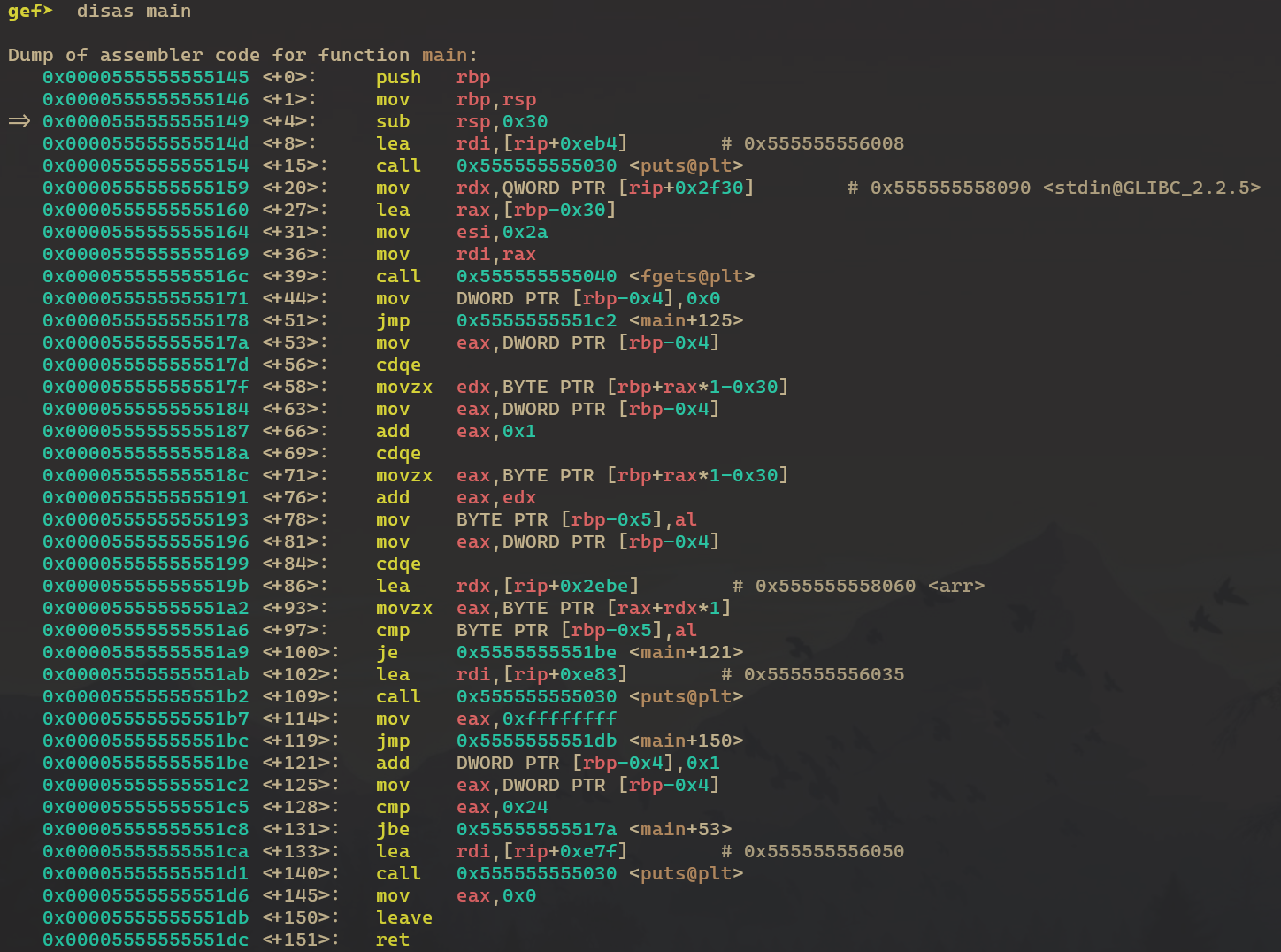
0x000055555555519b <+86>: lea rdx,[rip+0x2ebe] # 0x555555558060 <arr>main+86 is where arr gets loaded from memory. it is nice gef shows the address of arr, making things easier :) Then by inspectng the memory using the command:
x/40z 0x555555558060All values are nicely presented on the screen.
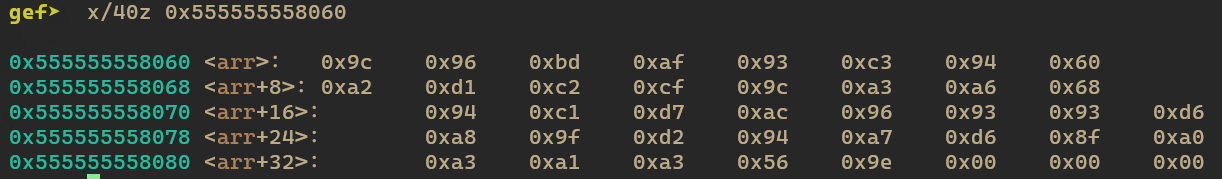
Knowing the flag format is HTB{…}, applying the first two characters to the algorithm and we can comfirm that 0x9C take away 0x48(“H” in ascii) is 0x54, which is ‘T’ in ascii. 0x96 take away 0x54(“T” in ascii) is 0x42, which is ‘B’ in ascii. By having the previous character and the arr, we can calculate the rest of the characters.
With all that, let’s write an exploit to get the flag!!!
Exploit
arr = [0x9c, 0x96, 0xbd, 0xaf, 0x93, 0xc3, 0x94,
0x60, 0xa2, 0xd1, 0xc2, 0xcf, 0x9c, 0xa3,
0xa6, 0x68, 0x94, 0xc1, 0xd7, 0xac, 0x96,
0x93, 0x93, 0xd6, 0xa8, 0x9f, 0xd2, 0x94,
0xa7, 0xd6, 0x8f, 0xa0, 0xa3, 0xa1, 0xa3,
0x56, 0x9e]
c = "H"
flag = "H"
for a in arr:
# get new character
new_n = bytes.fromhex(hex(a - ord(c))[2:]).decode('utf-8')
# append to the flag
flag += new_n
# update the current character
c = new_n
print(flag)Run the script and we get the flag.
HTB{4_d00r_cl0s35_bu7_4_w1nd0w_0p3n5!}Appendix
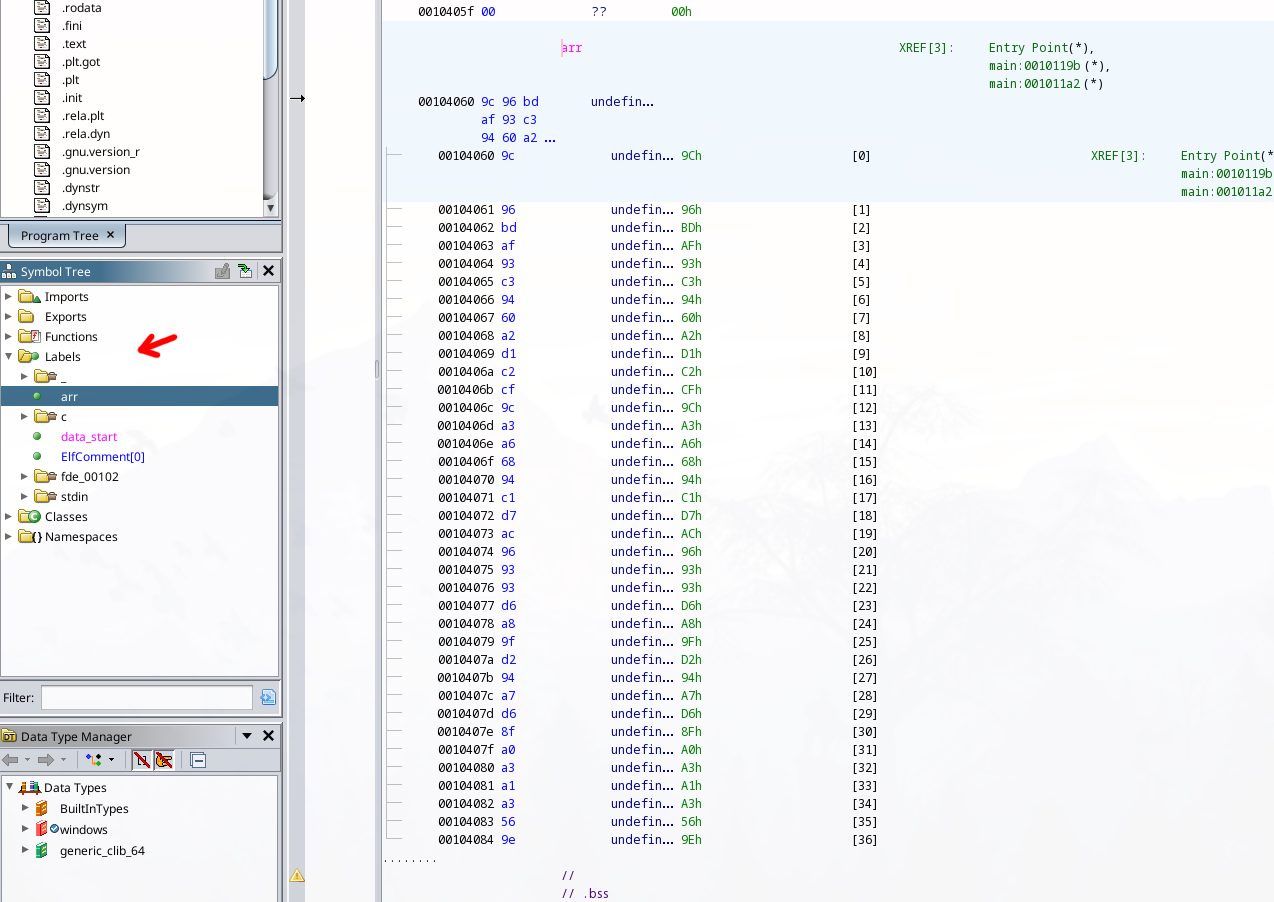
While writing the writeup, I discovered that the arr array can also be found under the the Symbol tree in Labels tab.